Authors:
(1) Kenan Begovic, currently a Ph.D. candidate in Computer Science at Qatar University. He received his MS in Information and Computer Security from University of Liverpool;
(2) Abdulaziz Al-Ali ,received the Ph.D. degree in machine learning from the University of Miami, FL, USA, in 2016 and he is currently an Assistant Professor in the Computer Science and Engineering Department, and director of the KINDI Center for Computing Research at Qatar University;
(3) Qutaibah Malluhi, a Professor at the Department of Computer Science and Engineering at Qatar University (QU).
Table of Links
- Abstract and 1 Introduction
- 2. On crypto-ransomware behavior and methodology
- 3. Detection of encryption
- 4. Conclusion
- Declaration of Competing Interest, CRediT authorship contribution statement, Data availability, and References
ABSTRACT
The ransomware threat has loomed over our digital life since 1989. Criminals use this type of cyber attack to lock or encrypt victims’ data, often coercing them to pay exorbitant amounts in ransom. The damage ransomware causes ranges from monetary losses paid for ransom at best to endangering human lives. Cryptographic ransomware, where attackers encrypt the victim’s data, stands as the predominant ransomware variant. The primary characteristics of these attacks have remained the same since the first ransomware attack. For this reason, we consider this a key factor differentiating ransomware from other cyber attacks, making it vital in tackling the threat of cryptographic ransomware. This paper proposes a cyber kill chain that describes the modern crypto-ransomware attack. The survey focuses on the Encryption phase as described in our proposed cyber kill chain and its detection techniques. We identify three main methods used in detecting encryption-related activities by ransomware, namely API and System calls, I/O monitoring, and file system activities monitoring. Machine learning (ML) is a tool used in all three identified methodologies, and some of the issues within the ML domain related to this survey are also covered as part of their respective methodologies. The survey of selected proposals is conducted through the prism of those three methodologies, showcasing the importance of detecting ransomware during pre-encryption and encryption activities and the windows of opportunity to do so. We also examine commercial crypto-ransomware protection and detection offerings and show the gap between academic research and commercial applications.
1. Introduction
The incursion of digital and online lifestyles in almost every segment of our lives has brought multiple consequences related to dependence on integrity and availability of information in business and personal matters. One of those consequences is our inability to live, work or even receive life-dependent services like medical treatment or water and electricity supply if related digital resources and data are unavailable or compromised. Cybercrimes are seeing significant growth across all geographies, with ransomware being the leading type of attack (Singleton et al., 2021). Ransomware is a type of attack where malicious actors utilize multiple tactics and techniques to gain the capability to lock or encrypt a victim’s data. This attack usually results in an ultimatum where the victim-user either pays for unlocking or decryption keys or faces losing all their data. Due to the already mentioned dependency on digital lifestyle, data is constantly growing in importance, creating an environment for a very lucrative business for ransomware gangs since the first recorded attack in 1989. While crypto-ransomware is a more common type of attack and lock-ransomware is in the decay (Berrueta et al., 2019), the latter is still relevant, especially in the mobile platforms (Su et al., 2018). According to a Fortinet survey, ransomware grew by 1070% across different industry verticals between July 2020 and June 2021 (Fortinet, 2021). Critical services like the health sector, especially in the age of the COVID19 pandemic, have been particularly vulnerable and targeted—the U.S. Health and Human Services Department has tracked 82 ransomware attacks in the first five months of 2021. The average cost of the incident in the U.S. health sector was around USD1.27 million, even though only USD131,000 was the average cost of the ransomware payment (U.S. Department of Health and Human Services Cybersecurity Program, 2021). The rest of the cost was distributed across lost business costs, including increased customer turnover, lost revenue due to system downtime, and the increasing cost of acquiring new business due to diminished reputation. Depending on the industry and geography, in other sectors worldwide, the ransom ranged between USD7.75 million and USD0.37 million, making the average cost of ransomware incidents in 2021 USD1.85 million (Sophos, 2021). The ransomware threat goes even further, with the Conti ransomware group announcing their support for the Russian invasion of Ukraine at the end of February 2022 and active participation in cyber warfare utilizing their capabilities and the available access to various assets worldwide (Russia-based ransomware group Conti issues warning to Kremlin foes | Reuters).
Despite all the reporting and high-profile cases of ransomware attacks, they continue to flourish and grow in sophistication and effectiveness. The reason for this probably lies in the fact that, according to Fortinet’s survey in 2021, 96% of companies that were already victims of ransomware gangs responded that they were moderately ready for the ransomware attack, even though 16% of them suffered from three or more attacks (Fortinet, 2021).
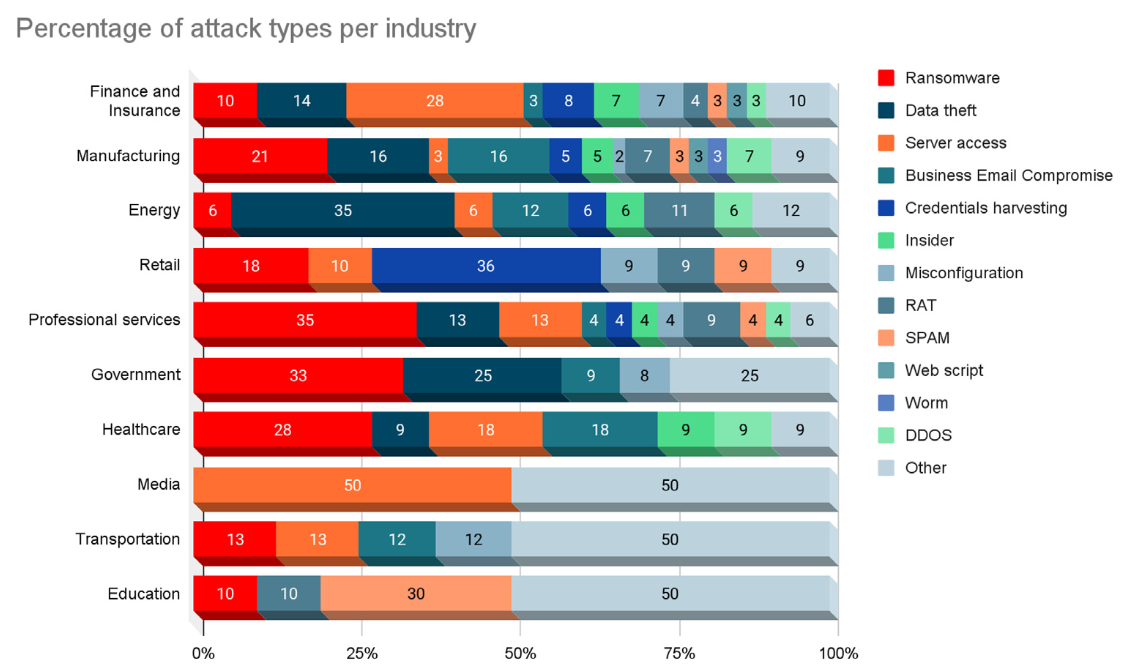
As shown in Fig. 1, in industries like Professional Services, Government, and Healthcare, the percentage of ransomware attacks as a portion of all cyber attacks is 35%, 33%, and 28%, respectively, making this type of attack by far the most common attack overall (Singleton et al., 2021).
Nevertheless, another trend was noticed in Sophos’ research on the state of ransomware. The malicious ransomware actors are moving away from generic and automated large-scale attacks to more targeted attacks executed with precision and persistence (Sophos, 2021). A review of the available data on modes of ransomware groups’ operation points to apparent similarities with the Advanced Persistent Threat modus operandi. This observation partially explains the increase in the difficulty of detecting and defending against these attacks compared to defending against malware like common viruses, trojans, or worms.
In the targeted crypto-ransomware attack, the malicious actor uses various techniques to gain the capability to encrypt the victim’s data. Such techniques evolve, becoming more focused (Sophos, 2021) and using precise no-noise attacks on the networks (Wang et al., 2018). Despite the shifting of techniques and some tactics, cryptographic ransomware carries one differentiating characteristic that separates it from malware: the capability and goal of encrypting victims’ data so that only malicious actors can decrypt it upon the ransom payment.
In this survey, existing proposals of pre-encryption and encryption detection techniques were reviewed to show their importance in countering ransomware and the possibility of being the ultimate solution for eliminating this threat. Detecting and countering crypto-ransomware has long been at the forefront of scholarly research. With the advent of the COVID-19 pandemic, motivation for ransomware attacks increased, and research interest in this topic has grown to an ever-larger extent. Most pre-encryption and encryption detection solutions operate in a host-based environment focusing on file system and kernel activity monitoring. However, some detection solutions focus on network communication inside local target networks and communication with command and control servers. The latter algorithms do not necessarily utilize network information to detect DNS-based indicators of compromise (IOC) but also deep packet inspection to detect cryptographic key delivery and exfiltration. The comprehensive set of algorithms and techniques to detect pre-encryption and encryption varies from simple decoys placement and file integrity monitoring to complex machine learning (ML) models trained on monitoring systems’ behavior during encryption and encryption-related operations, such as key generation. The survey also focuses on encryption-related detection in crypto-ransomware, and any further references to ransomware are related to the encryption of victims’ data by malicious actors with the purpose of extortion.
After introducing the topic of cryptographic ransomware, this paper covers related survey-like works available at the time of writing in the section 1.1 Related Work. Further, we propose a cyber kill chain to describe cryptographic ransomware attacks and discuss each of the defined phases in the kill chain, describing the behavior and methodology of attacks. In the survey part of the paper, we review research on the detection of activities related to the Encryption phase as described in the discussion of the proposed cyber kill chain. We also provide a brief survey of commercial solutions and usage of encryption detection outside of the crypto-ransomware use case.
1.1. Related work
Several surveys related to ransomware have been published, primarily focusing on defining the characteristics of ransomware attacks. However, there were no previous attempts to build a survey of detection techniques related to encryption as a hallmark of ransomware attacks.
Recent literature on ransomware threats is largely focused on three main streams. The first stream revolves around identifying recent ransomware threats based on static and dynamic analysis developed by the scientific community. The second stream aims to classify ransomware threats without necessarily focusing on detection algorithms. Finally, the third stream engages with holistic approaches to ransomware techniques and tactics. The following will briefly present these studies.
With regard to the first stream, Moussaileb et al. (2021), in their survey of ransomware threats to Windows operating systems, have unified all detection techniques based on static and dynamic analysis developed by the scientific community since 2014. This survey treats both crypto and locking ransomware types and, despite the title and general topic of the paper, covers some Android ransomware cases as well. The existing surveys focus on crypto ransomware strictly (Berrueta et al., 2019), noting the difficulty of surveying this novel topic since data from various papers is impossible to compare due to different metrics and approaches to ransomware.
Regarding studies focusing on the second stream, in an earlier attempt to survey research on ransomware, Alrimy et al. (2018) provided a comprehensive classification of ransomware attacks but with few details on detection algorithms. Also worth mentioning is a paper by Eze et al. (2018), that attempted a holistic examination of ransomware techniques and tactics in a very general and brief manner. Other survey-like papers focus on the evolution of the ransomware phenomenon (Zavarsky and Lindskog, 2016) or actual empirical data about real-world attacks (Connolly et al., 2020). In their survey of ransomware detection solutions, Herrera Silva et al. (2019) focus on identifying and listing all the detection and prevention parameters identified in the surveyed research, and they consider situational awareness concerning the same.
About the third stream, which takes more innovative approaches, more comprehensive surveys (Oz et al., 2022) cover all available varieties of platforms targeted by ransomware and consider the historical context and chronology of ransomware development. Other similar works (Dargahi et al., 2019) take the systematization of ransomware features’ taxonomy as a center of their proposal, and, similar to ours, the authors propose a cyber kill chain that attempts to describe and encompass all ransomware behavior observed so far. Also, some proposals focus on certain operating systems like Android (Ameer et al., 2018), Windows (Moussaileb et al., 2021; Reshmi, 2021; Naseer et al., 2020), or methods and tools in detection like a machine and deep learning and big data (Urooj et al., 2022; Bello et al., 2021). Finally, some proposals seek to build benchmarks for researchers who want to introduce more innovative approaches in ransomware detection mechanisms (Maigida et al., 2019).
Cryptographic ransomware detection has interested the academic community and the cybersecurity industry. Methodologies and techniques for detection use static and dynamic analysis of components and actions belonging to the cryptographic ransomware lifecycle phases. Some focus on local user machines, user and program activities, and the state of files in memory and file systems. Others look at the network indicators of ransomware presence, ranging from detecting single ransomware based on its signature to complex heuristic techniques and machine learning algorithms looking at multiple stages of the ransomware lifecycle.
Digging deeper into the available literature, it is noticeable that only some research papers focus on the issue of encryption in crypto-ransomware. Those usually concentrate on machine learning algorithms (Kok et al., 2020a) or methods like frequency of encryption estimation (Mülders, 2017). Furthermore, approaches focusing on the state of files in the file system (Jethva et al., 2020; Jung and Won, 2018), monitoring of the hardware performance (Dimov and Tsonev, 2020), and even the energy consumption (Azmoodeh et al., 2018) show promising results in detecting encryption.
This paper aims to survey contributions to the research of encryption detection in ransomware and techniques valuable for detecting the ransomware Encryption phase. The analysis does not employ first-hand information like in some other more general surveys on the crypto-ransomware (Berrueta et al., 2019). Instead, it focuses on results in other scientific and industry-based propositions with a strong focus on encryption detection. The outline of the contributions of this paper relative to the recent ransomware surveys can be summarized as follows:
-
Compared to other survey papers in the field, this survey provides a deeper dive into the detection of encryption by compartmentalizing the detection of encryption techniques and treating them as independent cases, even if they are part of a hybrid solution.
-
We identify a widening gap between richly-diverse academic literature on the detection of encryption techniques on the one hand and commercial implementations in market-leading solutions on the other.
-
We provide an overview of some of the key challenges and, in our view, misconceptions when approaching the topic of crypto-ransomware.
-
We present the need for a better organized cyber kill chain that describes the modern crypto-ransomware attack.
-
We propose a needs-based, field-informed contemporary cyber kill chain.
For completeness, an apt description and classification of cryptographic ransomware attacks in their methodologies and phases will be presented with a brief classification of detection techniques.
This paper is available on arxiv under CC BY 4.0 DEED license.